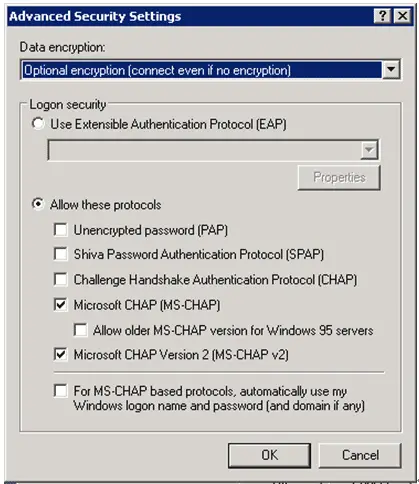
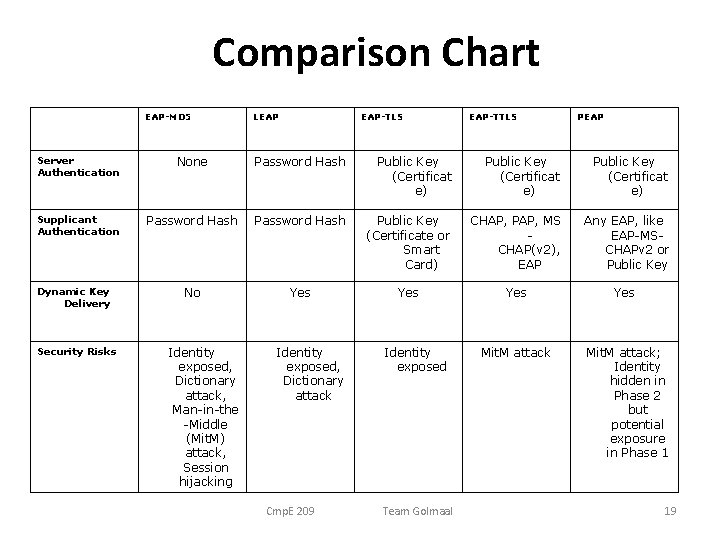
Table 1 from Network access authentication infrastructure using EAP-TTLS on diameter EAP application | Semantic Scholar
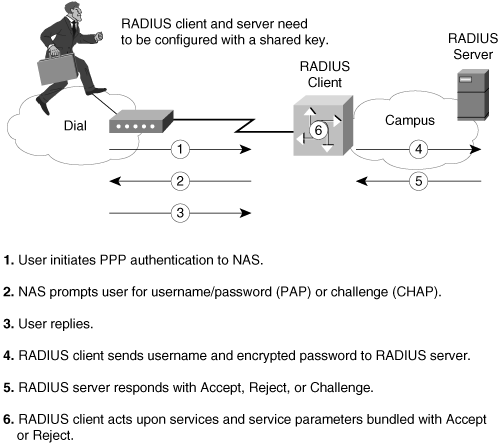
Authentication and Identity Protocols :: Chapter 2. Basic Security Mechanics and Mechanisms :: Wireless lan security :: Networking :: eTutorials.org
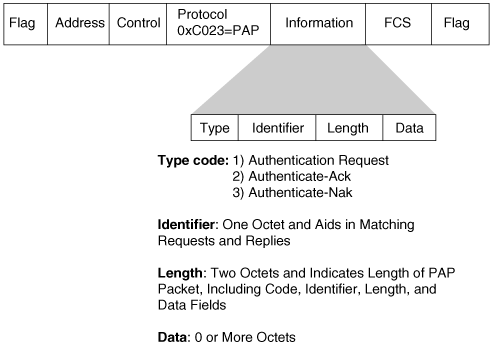
Authentication and Identity Protocols :: Chapter 2. Basic Security Mechanics and Mechanisms :: Wireless lan security :: Networking :: eTutorials.org
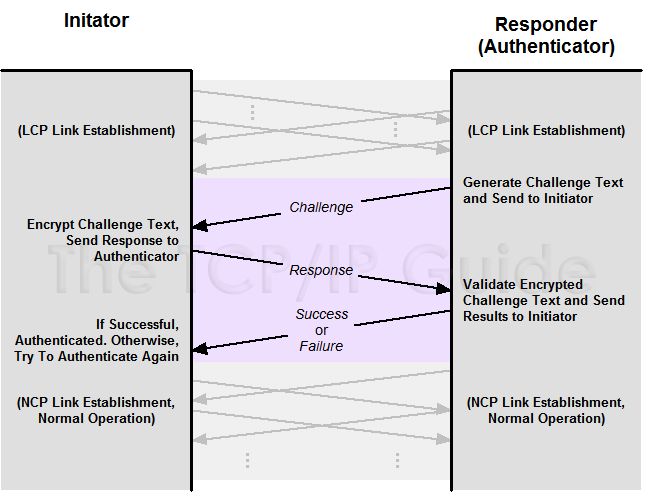
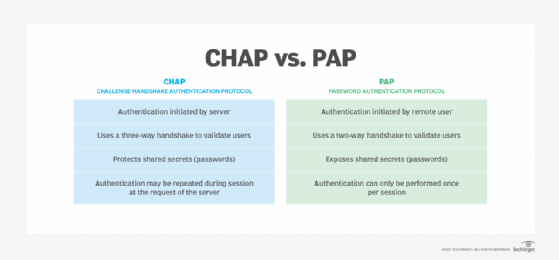
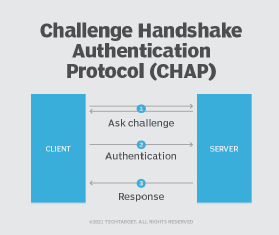
The TCP/IP Guide - PPP Authentication Protocols: Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP)

![MS-CHAP]: Overview | Microsoft Docs MS-CHAP]: Overview | Microsoft Docs](https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-chap/ms-chap_files/image001.png)



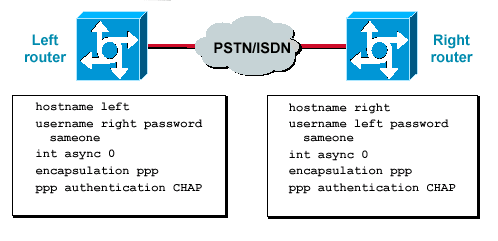
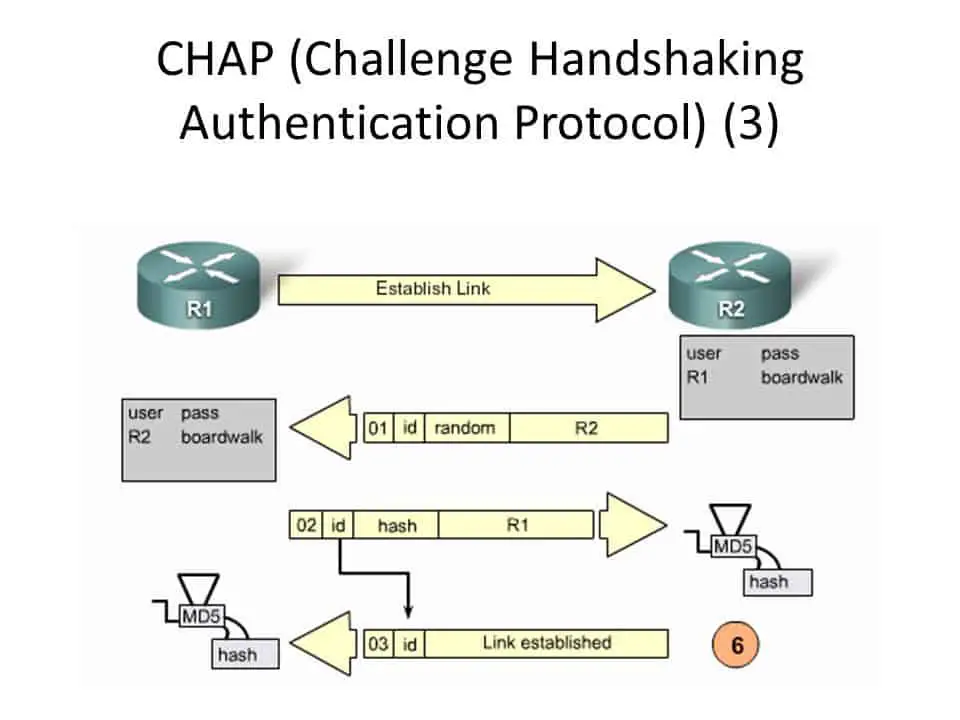



![Inner Method] Inner Method]](https://www.manual.sato-global.com/printer/clnxplus/images/GUID-8D316995-ABC8-4DF7-B467-1D00D1628FB6-low.png)